UPDATE starting from firmware 3.5.0 it’s totally different, see http://developers.sonoff.tech/sonoff-diy-mode-api-protocol.html
It’s possible to flash Espurna on the Sonoff Mini using Diy mode via software.
What you need
- A Sonoff Mini
- A mobile device capable of creating an Access Point and which can install eWelink app
- A PC:
- with Wi-Fi
- running GNU/Linux (I used Ubuntu 19.10)
- with a running web server
- with
gitinstalled
Procedure
Here’s the steps I took to do it:
-
Download and compile Espurna
$ mkdir ~/project $ cd ~/project $ git clone https://github.com/xoseperez/espurna $ cd espurna/code $ pio run -e itead-sonoff-mini -
Install and configure eWelink app

-
Update Sonoff Mini firmware (currently the latest version is 3.3.0, I’ve read you need 3.1.0 at least)
-
Shutdown the device (detach it from mains current)
- Enable OTA
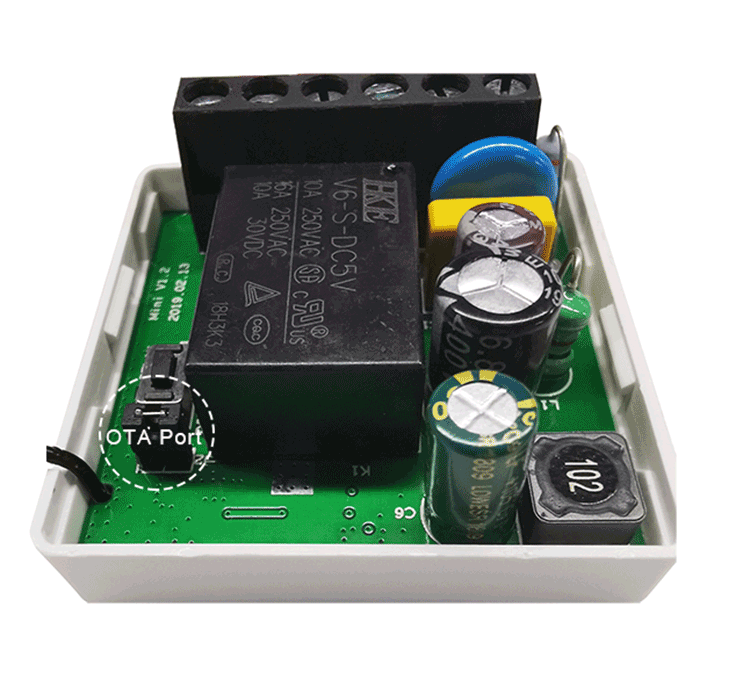
- Create an Access Point with your phone. These must be the parameters:
- SSID:
snonffDiy - pre shared key (password):
20170618sn - band: 2.4 GHz
- SSID:
- Boot the device (attach it to mains current)
- Wait until it connects to the AP (the blue led double pulses)
- Connect the PC to the same Wi-Fi
-
Search for the Sonoff Mini device on the Wi-Fi network
$ avahi-browse -t -r _ewelink._tcp + wlp1s0 IPv4 eWeLink_10009b8ed6 _ewelink._tcp local = wlp1s0 IPv4 eWeLink_10009b8ed6 _ewelink._tcp local hostname = [eWeLink_10009b8ed6.local] address = [192.168.43.200] port = [8081] txt = ["data1={"switch":"off","startup":"off","pulse":"off","pulseWidth":500,"rssi":-29}" "seq=1" "apivers=1" "type=diy_plug" "id=10009b8ed6" "txtvers=1"]Keep track of the
deviceidwhich is, in my case,1009b8ed6. -
Test if everything works as expected
$ curl -XPOST --data '{ "deviceid": "10009b8ed6", "data": {} }' http://192.168.43.200:8081/zeroconf/info; echo {"seq":2,"error":0,"data":"{\"switch\":\"off\",\"startup\":\"off\",\"pulse\":\"off\",\"pulseWidth\":500,\"ssid\":\"sonoffDiy\",\"otaUnlock\":false}"} -
Unlock OTA updates
$ curl -XPOST --data '{ "deviceid": "10009b8ed6", "data": {} }' http://192.168.43.200:8081/zeroconf/ota_unlock; echo {"seq":2,"error":0} -
Put file in a web server
$ cd ~/public_html $ cp ~/project/espurna/code/.pio/build/itead-sonoff-mini/firmware.bin . $ chmod a+r firmware.bin -
Test url
$ curl -s http://192.168.43.53/~max/firmware.bin --output - | sha256sum e9e7d72d2c2a8b25678cab7ded20645c5e37c60459cbe6ba1448ed3a62f72b72 $ sha256sum ~/public_html/max/firmware.bin e9e7d72d2c2a8b25678cab7ded20645c5e37c60459cbe6ba1448ed3a62f72b72 firmware.binYou will need the sha256sum value in a minute.
-
Do the OTA, keep attention to use the right
deviceid,sha256sumandipvalues$ curl -XPOST --data '{ "deviceid": "10009b8ed6", "data": { "downloadUrl": "http://192.168.43.53/~max/firmware.bin", "sha256sum": "e9e7d72d2c2a8b25678cab7ded20645c5e37c60459cbe6ba1448ed3a62f72b72" } }' http://192.168.43.200:8081/zeroconf/ota_flash; echo {"seq":3,"error":0}
Done.